If configurations or unanticipated software vulnerabilities exist, leaving the SSH port open and unrestricted may allow incursions for public instances. Use these best practices to assist prevent intrusions:
Restrict your security group to allow incoming connections to port 22 from trusted IPs only, such as corporate network Ips.
Typically, to connect to a remote instance in AWS, you enter your username and password into a client like Telnet or Putty. Using a password that is too long every time you want to start a session is annoying and insecure.
You can increase security by using keypairs, which are made up of a public key and a private key. Your private key is kept secret and your public key is kept on the host you want to connect to. These keys can be used in saved sessions and are encrypted. When you log in remotely to the host, it assists you in using your private key and establishes a connection without requesting a password.
It’s still safer to store a private key than storing a password, as the private key is encrypted.
This blog demonstrates how to switch over to key-based SSH authentication, which is more secure because it allows only the key’s owner to log in. In this illustration, we’re using a Windows PC and PuTTY as our SSH client.
1. Download Putty from https://putty.org/
 2. Generate a private and public key pair using puttygen (its get’s installed, when you install putty)
2. Generate a private and public key pair using puttygen (its get’s installed, when you install putty)
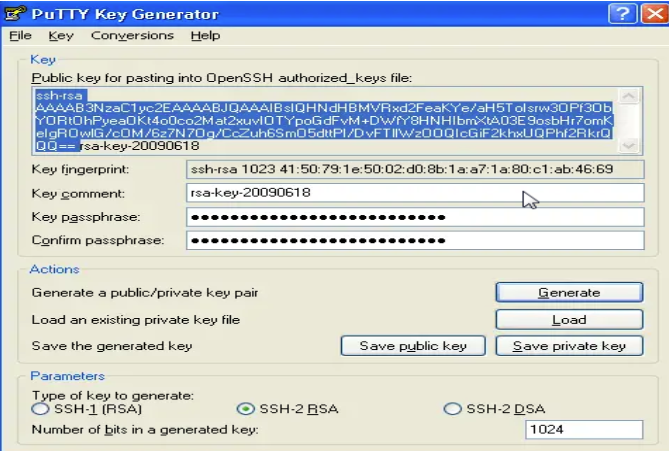
Open PuTTYgen , press Generate button, and keep moving the mouse, till the time keys are generated. Once the keys are generated, type your key passphrase (choose a “hard to guess” one. This is optional. You can continue without providing the passphrase). Save the Public key. Save the Private key.
 3.Configure your Linux server (create a user, save the public key)
3.Configure your Linux server (create a user, save the public key)
For this guide let’s assume your regular login name is test (replace it with one that you use regularly).
As root, on the shell, type:
adduser test –disabled-password
You will be asked to fill in some details such as the user’s real name (empty string is fine).
Now type:
su test
cd /home/test
mkdir .ssh
chmod 700 .ssh
cd .ssh
Then in that folder, create and edit a file called authorized_keys. With below commands
authorized_keys
In there, cut/paste your public ssh key, on ONE LINE (That is very important!!!). After you paste the key, save the file by pressing ESC key once on keyboard and typing :wq at the prompt
Note:
- Do not add the email@example.com at the end of the line.
- Do not add the BEGIN PUBLIC KEY or END PUBLIC KEY.
- Do not add the rsa-key-20090614 at the end.
- Make sure, there is ssh-rsa at the beginning.
The entry in the file should look similar to the one shown below
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAIBzPeFQv+295iKzuuPH0jA9449pSHVpCwXvCR9EstmYh…
Now change the permission (in the earlier step we gave 700 file permission to the ssh directory, thus all the files and folders inside this directory will have this permission ) to the authorized keys file by typing the below command at the prompt
Type:
chmod 600 authorized_keys2
4. Add Private key to PuTTY SSH authentication agent
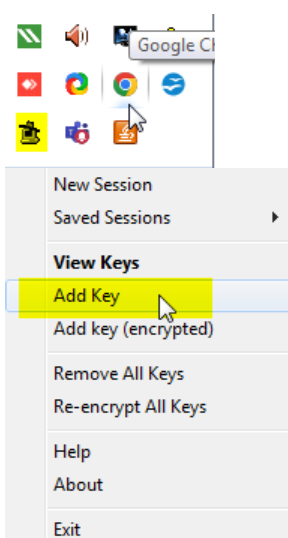
Start the PuTTY SSH authentication agent PAGEANT.EXE. (it get’s installed with Putty)
Once paegant is started, you will find it in the system tray. right-click its syspanel icon and select “add key”. Select your private key file, and type in your passphrase (if you have given it) when you add the key. The Pageant works as a passphrase keeper.
5. Use PuTTY to connect to your server
Open PuTTY and connect as test@ IP_address (IP address of the EC2 instance) to connect. For demo, I have given the IP address as 1.2.3.4.
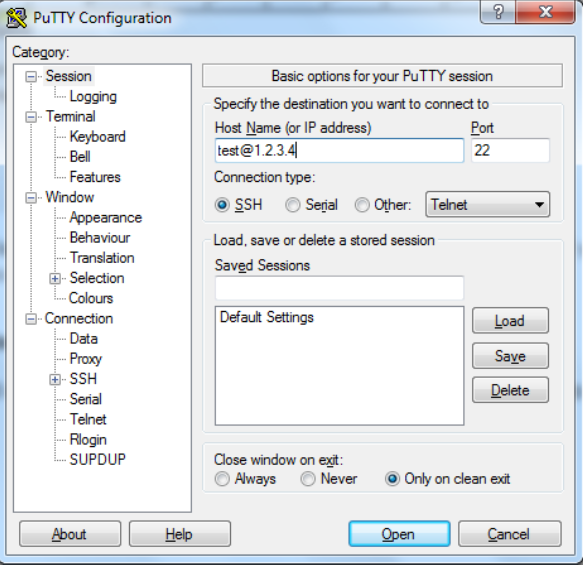
Click on open, and see you log in without a password.
UseCases when the above method can be helpful
- If a user in your organization requires access to the system by using a separate key pair, you can generate a new keypair and copy the public key in the file ~/.ssh/authorized_keys
- If someone has a copy of the private key (.pem file) and you want to prevent them from connecting to your instance (for example, if they’ve left your organization), you can delete the public key on the instance and replace it with a new one.
- If you create a Linux AMI from an instance, the public key material is copied from the instance to the AMI. If you launch an instance from the AMI, the new instance includes the public key from the original instance. To prevent someone who has the private key from connecting to the new instance, you can remove the public key from the original instance before creating the AMI.
To add or replace a key pair, you must be able to connect to your instance. If you’ve lost your existing private key or you launched your instance without a key pair, you won’t be able to connect to your instance and therefore won’t be able to add or replace a key pair. If you’ve lost your private key, you might be able to retrieve it. If you launched your instance without a key pair, you won’t be able to connect to the instance unless you chose an AMI that is configured to allow users another way to log in.
To add or replace a key pair
- Create a new key pair using the Amazon EC2 console or a third-party tool (Putty).
- Retrieve the public key from your new key pair.
- Connect to your instance using your existing private key.
- Using a text editor of your choice, open the .ssh/authorized_keys file on the instance. Paste the public key information from your new key pair underneath the existing public key information. Save the file.
- Disconnect from your instance, and test that you can connect to your instance using the new private key fileDisconnect .
- If you’re replacing an existing key pair, connect to your instance and delete the public key information for the original key pair from the .ssh/authorized_keys file.
For more software engineering related blogs, follow here.






Add comment